Which Of The Following Is An Advantage Of A Signature-based Detection System?
Which of the following is an advantage of a signature-based detection system?. Perform the following slops. Signature-based intrusion detection systems do not detect new attack methods for which. Which of the following is an inherent weakness of signature-based intrusion detection systems.
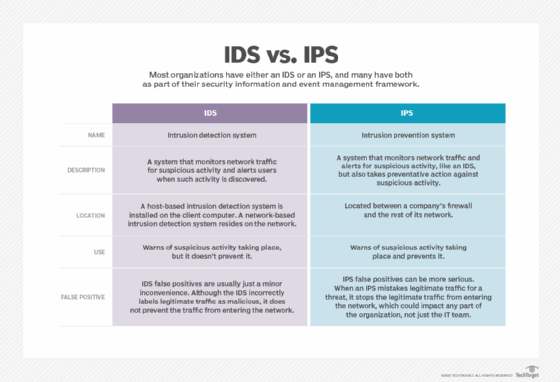
In addition if the system administrator has a clear understanding what network behavior theyre identifying signatures are easy to develop. The host-based intrusion detection system can detect internal changes eg such as a virus accidentally downloaded by an employee and spreading inside your system while a network-based IDS will detect malicious packets as they enter your network or unusual behavior on your network such as flooding attacks or protocol-specific attacks. A higher number of false positives.
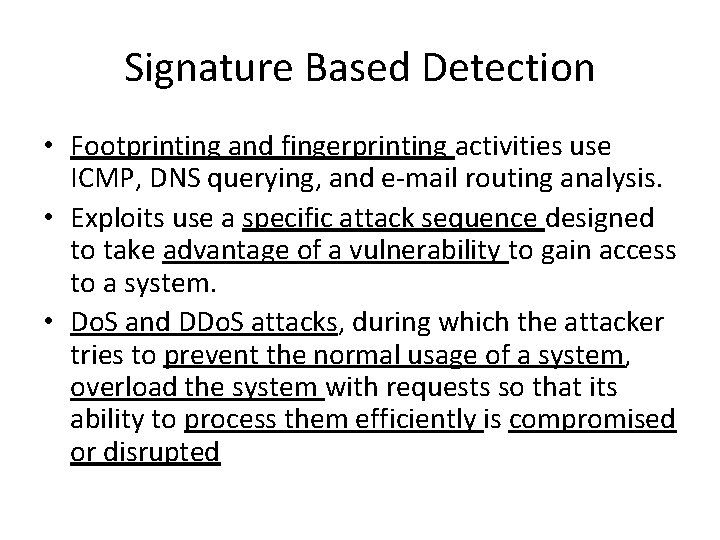
Each signature is assigned a number and name Which method for detecting certain types of attacks uses an algorithm to detect suspicious traffic is resource intensive and requires extensive tuning and maintenance. It allows the recipient of data to prove the source and integrity of data. Signature-based detection can offer very specific detection of known threats by comparing network traffic with the threat signature database.
Which of the following statement is most accurate of digital signature. A host based system can analyze the decrypted traffic to find attack signature-thus giving them the ability to monitor encrypted traffic. However signature-based security systems will not detect zero-day exploits.
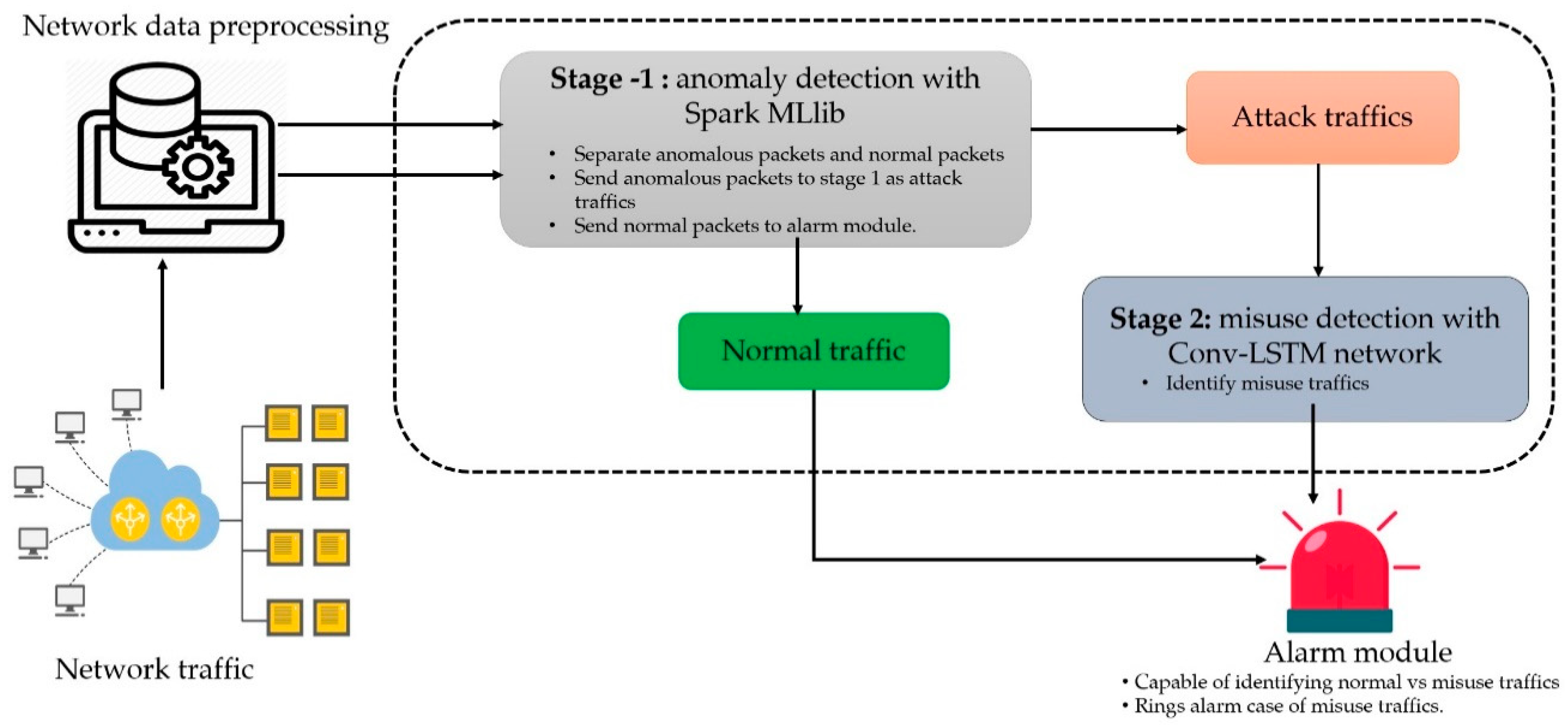
Signature based detection system also called misuse based this type of detection is very effective against known attacks 5. Configure the WiFi controller. The detection can be enhanced if the network traffic inside the network can be made to learn specific patterns thus reducing false positives.
Firstly its easy to fool signature-based solutions by changing the ways in which an attack is made. IX using the most secure encryption and protocol available. A written expression of an item of concern protocol port service application user and IP address and one or more actions to take when the item of concern appears in traffic.
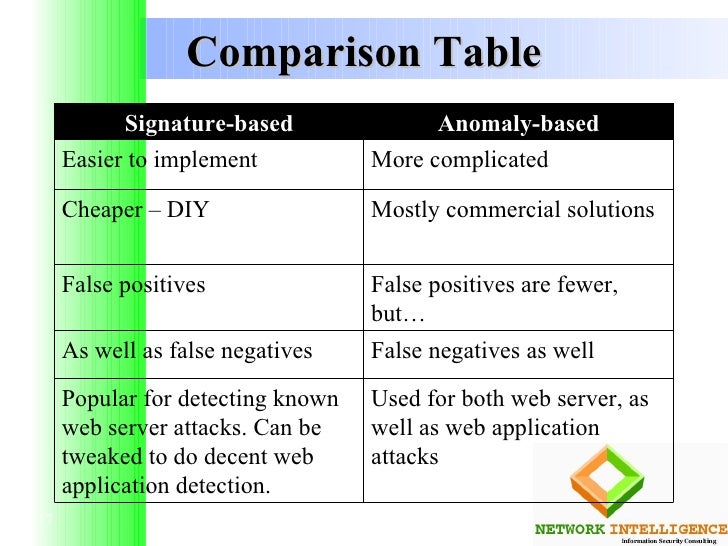
- Signature-based detection has the advantage of a high processing speed as pattern matching occurs very quickly. Describe the advantages and disadvantages of signature-based detection.
Novel attacks cannot be detected as the only execute for known attacks 2.
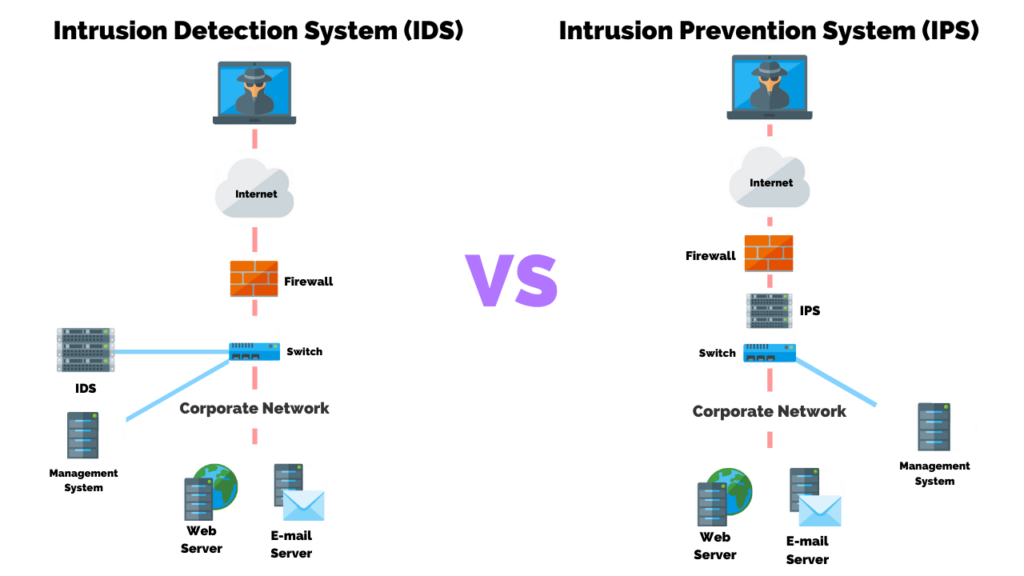
SY0-601 CompTIA Security Exam 2021 Questions and Answers. Signature-based intrusion detection systems do not detect new attack methods for which. It implies that misuse detection requires specific knowledge of given intrusive behaviour. A signature-based intrusion detection system SIDS monitors all the packets traversing the network and compares them against a database of attack signatures or attributes of known malicious threats much like antivirus software. It is not true that signature-based intrusion detection systems only run on the windows operating system. They can monitor all users activities which is not possible in a network based system They are capable of identifying attacks that originate from inside the host. A signature-based intrusion prevention system monitors the network traffic for matches to these signatures. Which of the following statement is most accurate of digital signature. An example of Signature based Intrusion Detection System is.
A signature-based intrusion detection system SIDS monitors all the packets traversing the network and compares them against a database of attack signatures or attributes of known malicious threats much like antivirus software. A higher number of false positives. Signature based detection system also called misuse based this type of detection is very effective against known attacks 5. - Signature-based detection has the advantage of a high processing speed as pattern matching occurs very quickly. Anomaly-based detection can help identify these new exploits. Configure the RADIUS server. A written expression of an item of concern protocol port service application user and IP address and one or more actions to take when the item of concern appears in traffic.



























Post a Comment for "Which Of The Following Is An Advantage Of A Signature-based Detection System?"